 ✕
✕
By Justin SabrinaUpdated on December 17, 2022
From early 2020, COVID-19 has spread widely across the world. Due to the need for epidemic prevention, many companies have suspended work and production, and schools have suspended classes. But in order to maintain normal operations, people can work from home and attend classes online. Zoom has become a necessity, it is the world's most popular video conferencing App. Office workers can use it to hold online meetings, and students can use it to learn knowledge in online classrooms. Thus, more and more people have found zoom vulnerabilities while using it. In this article, we will demonstrate these Zoom vulnerabilities and how to fix Zoom vulnerabilities issues. Additionally, we will recommend you an excellent tool to help you record Zoom meeting to local drive safely, so that you can refer back these segments at anytime.
CONTENTS
With the spread of the epidemic COVID-19, Zoom's users are increasing day by day. The safety issue has naturally become the focus of people's attention. Here we will list the main Zoom vulnerabilities issues.
# 1. User Data of Zoom was Leaked to Facebook
Some users stated that when Zoom App is launched on iOS device, Zoom will send users' info to Facebook without the user's consent, even if you are not a Facebook user. The following information will be sent to you when you run Zoom App.
Zoom response: Zoom admits that data sharing occurs because it gives users the option to log in to Zoom through the Facebook Software Development Kit (SDK). Since then, Zoom has deleted all related code and Facebook SDK to prevent such sharing in the future, which means protecting user information from being leaked.
# 2. Zoom Makes Windows Credentials Potentially Stolen
Zoom's Windows client chat function has a vulnerability in handling UNC (Universal Naming Convention) paths, it will causes Zoom may exposes users Windows info.
Zoom chat converts the UNC path into a clickable link on the Windows client. If someone clicks on the link, their Windows username and NTLM credential may be sent over the Internet to a site provided by a malicious user.
Zoom response: Zoom subsequently released a patched version to fix the vulnerability. The new version improves security and there is no risk of leaking credentials any more.
# 3. Zoom Doesn't Work Perfectly with iOS Devices
In the Mac version, there is a risk of unauthorized access due to the ability to elevate local privileges. Hackers exploited many iOS vulnerabilities through the Zoom App and targeted Apple users. Malicious users can use Zoom to install malware software.
It abuses the pre-installation script, decompresses it by itself, and automatically installs it on the device without the user's consent. It can also grant root access to unauthorized users.
Zoom response: Both Zoom and Apple have fixed the error in subsequent updates. Zoom has repaired its server settings, which allows Mac users to manually uninstall Zoom App from the menu bar. It also removes the App that use Zoom technology and are automatically installed on Mac computers without the Mac user's permission.
# 4. Zoom's End-to-End Encryption are Vulnerable
Zoom has been criticized by the Federal Trade Commission (FTC) for its "deceptive and unfair" encryption standards and policies. Because Zoom video conferences and calls are easily eavesdropped. Zoom told users that it provides end-to-end encryption, but in fact it uses a transmission method, not end-to-end.
* What is end-to-end encryption?
The host can publish the encryption key and distribute it to participants using public key technology.
What Zoom provides is a transmission. In terms of trust and security, real E2E is very different from this approach. In E2E, no one can disclose the content of the call except the parties in the video conference. Through Transport Layer Security (TLS), any party and Zoom Video Communication, Inc. itself and anyone who disrupts or successfully subpoenas Zoom has this right.
Zoom response: Zoom admitted that they used "E2E" in different ways. The data first enters the server of Zoom, and then enters your correspondent. Therefore, Zoom can understand and view customer video calls and chat content as needed.
# 5. "Zoom Bombings" and Meeting Disruptions
Another common problem on Zoom is "Zoom Bombing" by malicious users. The Zoom bomb is a nuisance where a third party breaks into the meeting without permission. The host can barely control the situation. They cannot decide who can enter the meeting, suspend user activity, or suspend the meeting.
Zoom response: Zoom has solved the "Zoom bombing" problem by introducing the following new features:
After we learned about the common Zoom vulnerabilities, it has been updated software to fix Zoom vulnerabilities.
Way 1. Thorough Management of ID, Password and URL
The management of Zoom ID and password are the basis of security measures. To prevent malicious users from breaking in during the meeting, please make sure that your ID and password are not leaked to the outside.
The same applies to the URL of the meeting. If the Zoom URL is posted in a place that anyone can see, such as SNS, it will increase the risk of the Zoom bomb entering the conference.
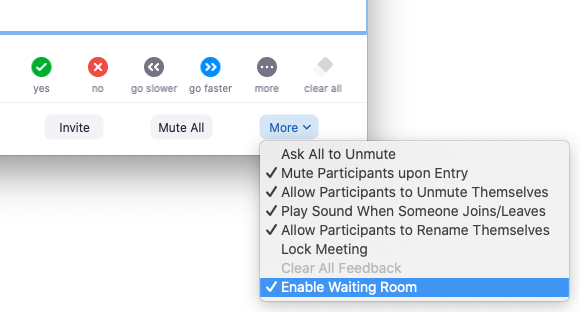
Way 2. Use "Waiting Room" Function
The new version of Zoom adds a feature called the "Waiting Room". After the waiting room is opened, other users will not be able to enter the meeting unless allowed by the host, including forcibly entered by malicious users.
This is a very good way to protect the Zoom meeting. This function provides a virtual waiting room for participants, allowing individual participants to join the meeting freely. By setting, you can only allow approved users to join the meeting directly without using the waiting room.
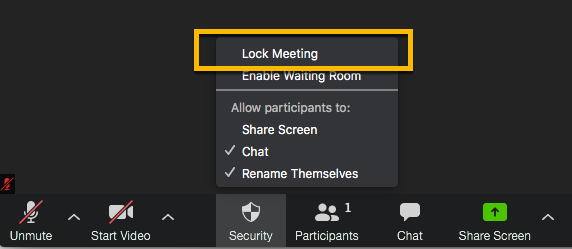
Way 3. Lock the Meeting
Locking the meeting provides you with greater security. It prevents other uncorrelated users from joining the meeting, even if they know your ID and the URL of meeting, they cannot enter a locked meeting.
To ensure safety, it is best to lock meeting when all participants are together in the meeting. It can prevent the Zoom bomb from being suddenly interrupted by malicious users.
Just select "Lock Meeting" from the "Security" button displayed on the menu bar at the bottom of the screen during the meeting.
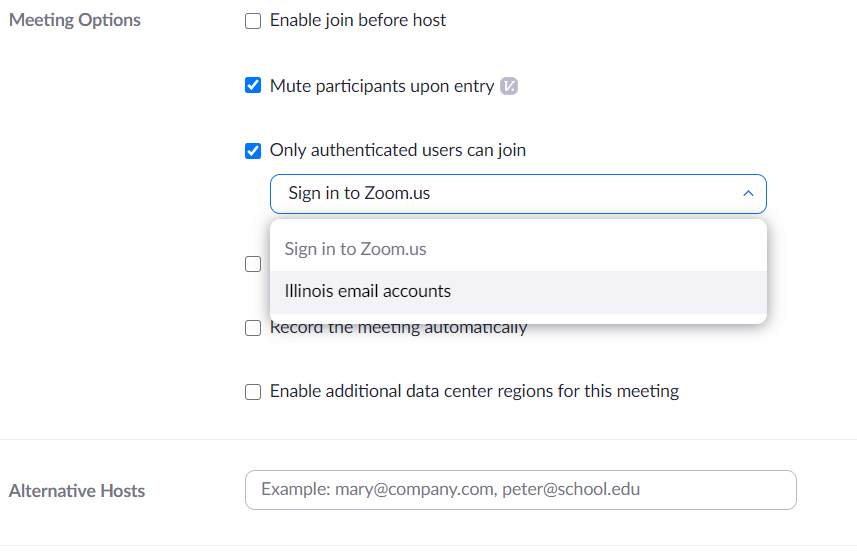
Way 4. Limit the Meeting Participants
In addition to the above two methods, you can also set who can join the Zoom meeting. If you set the email addresses of the people you want to invite in advance, those who haven't been invited will not be able to join the meeting from other accounts.
Similar to waiting room and lock meeting, it helps reduce the risk of third-party entry and reduce the zoom bombs of malicious users.
Select the "Meeting" section. And click the slider to the right of "Only authenticated users can join meetings" to turn it on.
Way 5. Use Zoom in Secure Network Environment
Since Zoom is online meeting, we recommend using it in a secure Internet environment. Regarding a secure Internet environment, there are 2 things to keep in mind.
1. It is dangerous to use on Free Wi-Fi / Public Wi-Fi
Using free Wi-Fi or public Wi-Fi for online meetings is dangerous. If you use Zoom on free Wi-Fi without a password, there is a risk of unauthorized access by malicious third parties. The same applies to public Wi-Fi that can be used by unspecified people such as cafes.
When you hold an online meeting, please make sure to use Zoom in a stable Internet environment.
2. Use a router with security measures
You should also understand router security when working remotely. When using Zoom, try to use a router with security measures to connect to Wi-Fi.
By correctly managing the router's port and setting the password, you can prevent others from illegally accessing it through the router and communications.
The above are the measures to fix Zoom vulnerabilities issues, in short, there are still certain Zoom vulnerabilities. In the next part, we are going to introduce you a tool, which can record Zoom meeting safely.
UkeySoft Screen Recorder is a useful and powerful Screen Recorder and Video Editor. If you are Zoom user, you can record Zoom meeting to local drive. Notably, you can record Zoom meeting without permission on your computer. Additionally, you can even change your Zoom background by yourself. And it can record video from YouTube, Vine, Vimeo, Hulu and more video format such as MP4, FLV, AVI, WMV, etc. losslessly.
Main Features of UkeySoft Screen Recorder:
UkeySoft Screen Recorder can work well with Windows and Mac computer, follow the guide below to record Zoom meeting to local drive by UkeySoft Screen Recorder.
(Tip: Turn on the Microphone and Webcam on your computer, to make sure your sound and face can be recorded in your recorded videos.)
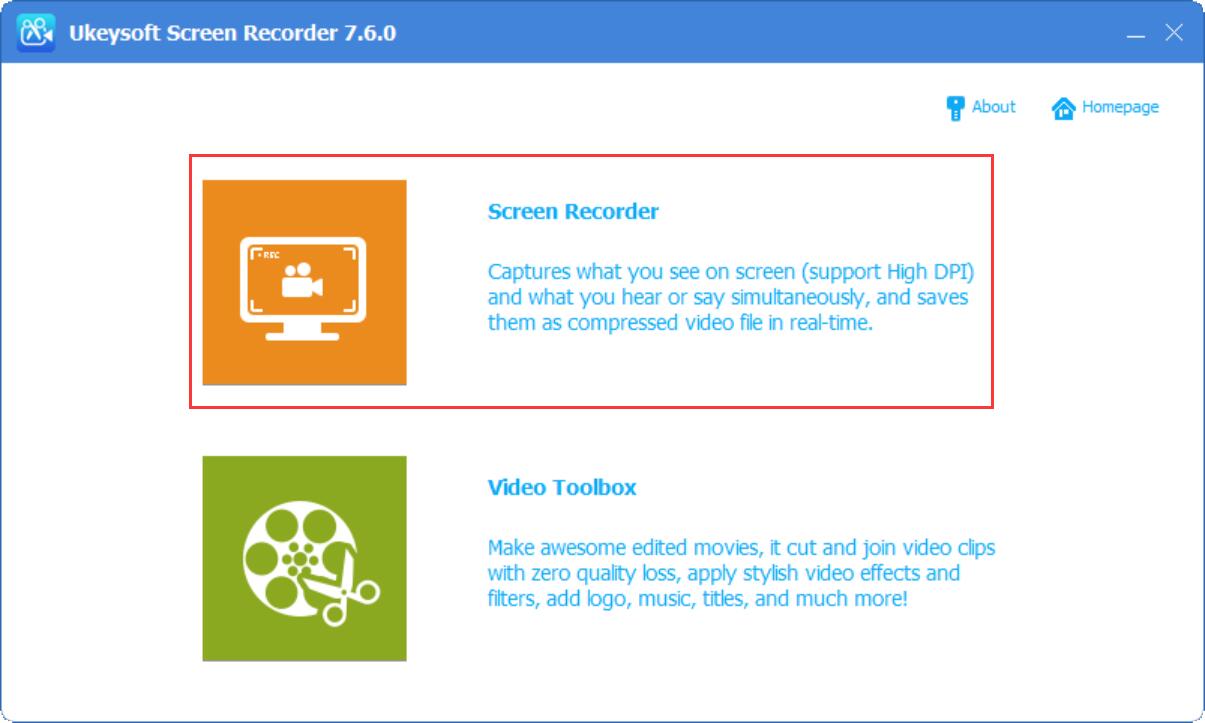
Step 1. Run UkeySoft Screen Recorder on Computer
Download, install UkeySoft Screen Recorder on your Mac/Windows computer, then run the software. To record a Zoom meeting, please choose "Screen Recorder" option.
Step 2. Adjust Computer Sound for Recording Zoom Meeting
To record your voice to in the meeting, please adjust "Computer sound and microphone" mode before you record the Zoom meeting.
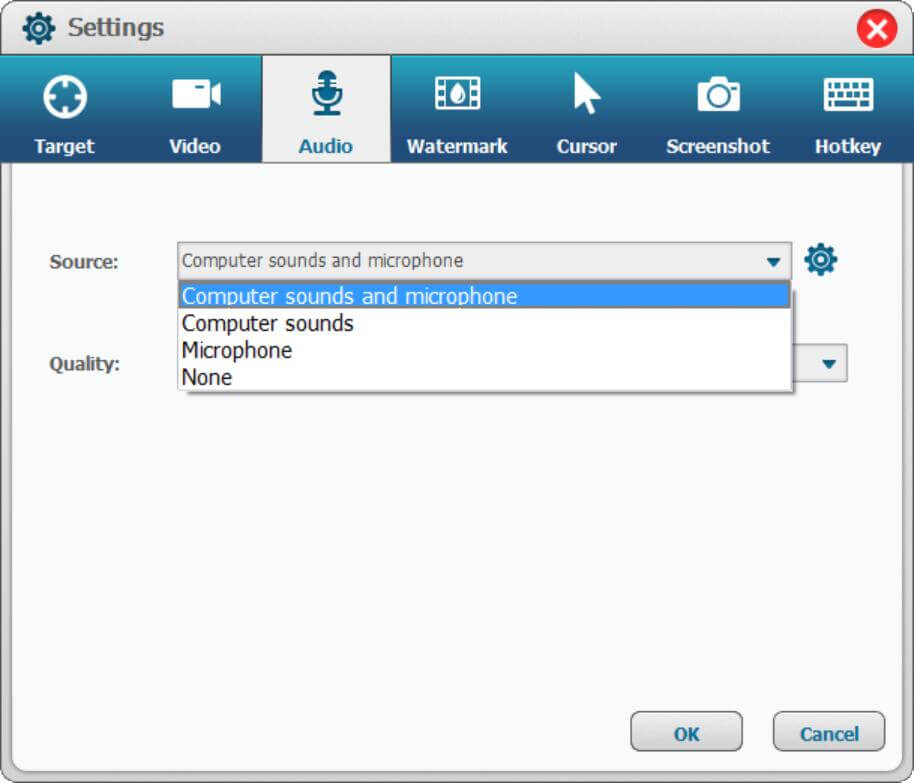
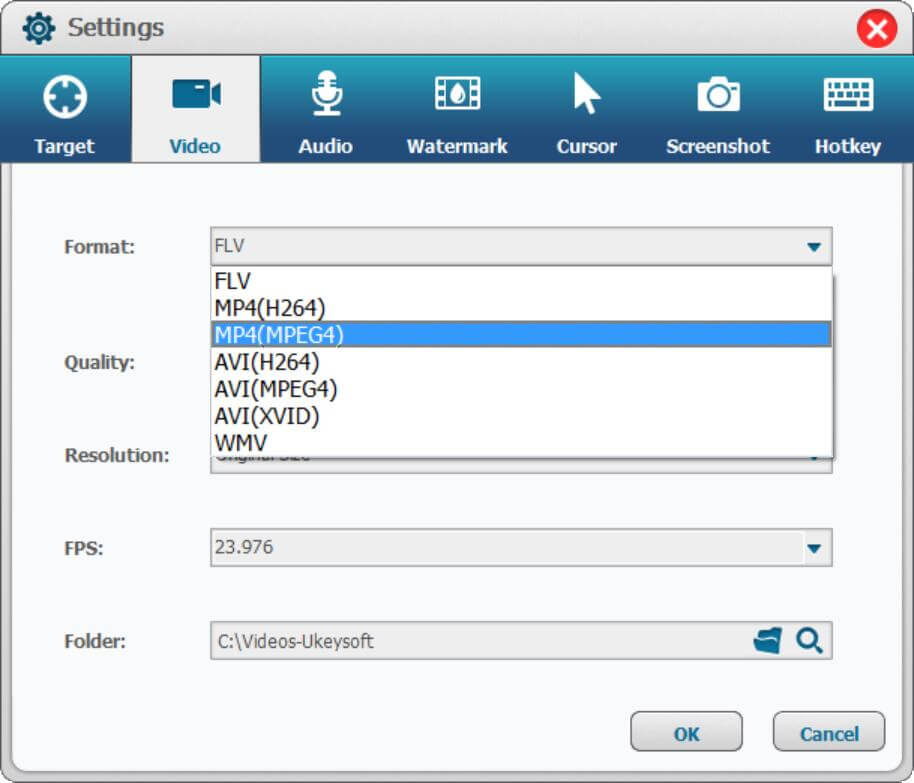
Step 3. Customize Output Settings for Zoom Meeting
Go to "Settings" > "Video", here you can record Zoom Video Calls as MP4, AVI, FLV and WMV, etc.
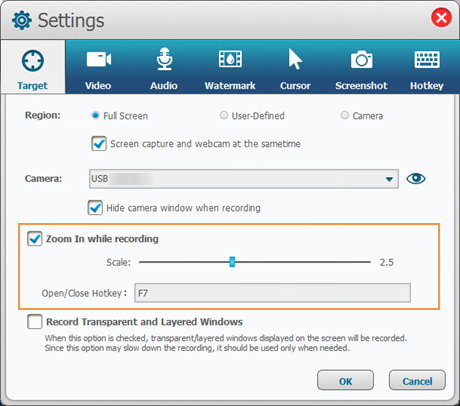
And you can adjust "Zoom in while recording" and adjust the scale from 1.5 to 4.0 according to your needs.
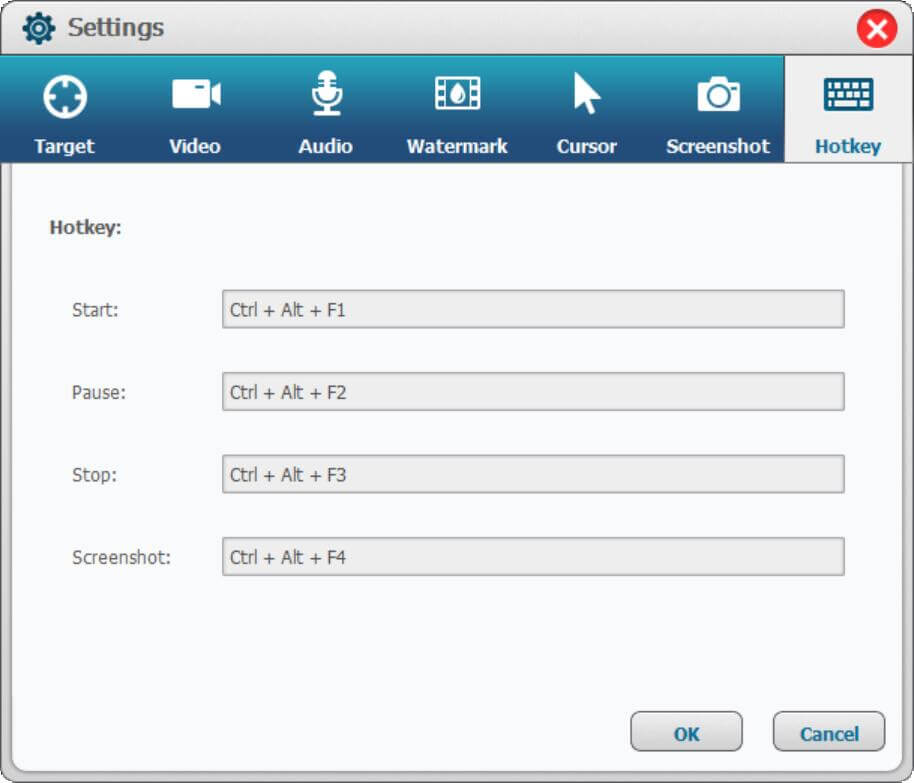
After start video recording, move the cursor to the area you want to zoom in, just click "Hotkey" icon in the top bar to move it, or start, pause or close recording Zoom video.
Step 4. Select Recording Area for Zoom Meeting
Go back to the home screen recorder to select the recording area for Zoom Meeting Calls: full screen, specific recording area or camera, to help you capture videos.
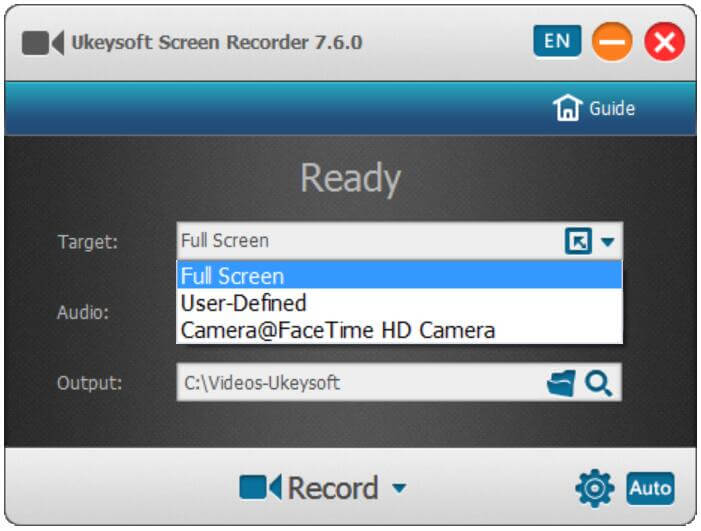
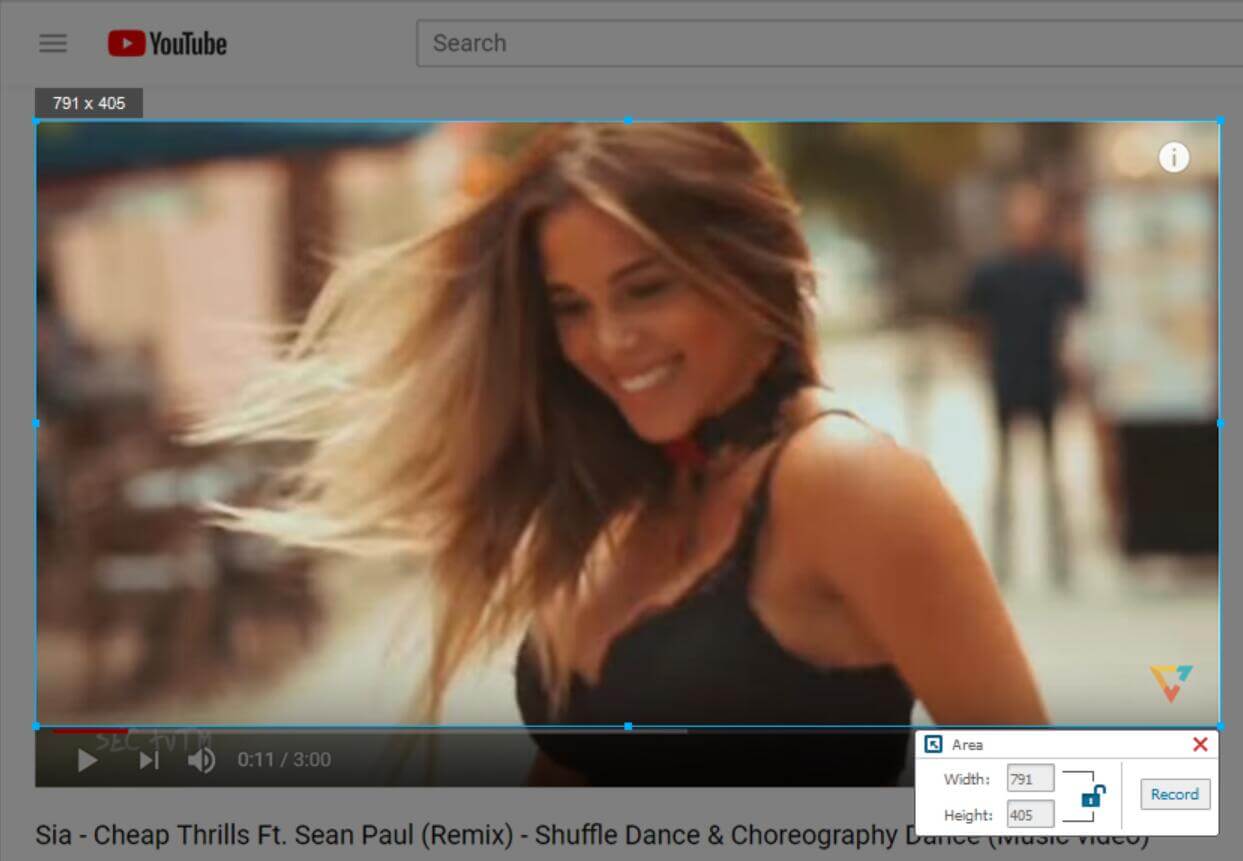
Step 5. Start to Record Zoom Meeting Safely
When all the settings are done, click "Record" button to record Zoom meeting to local drive.
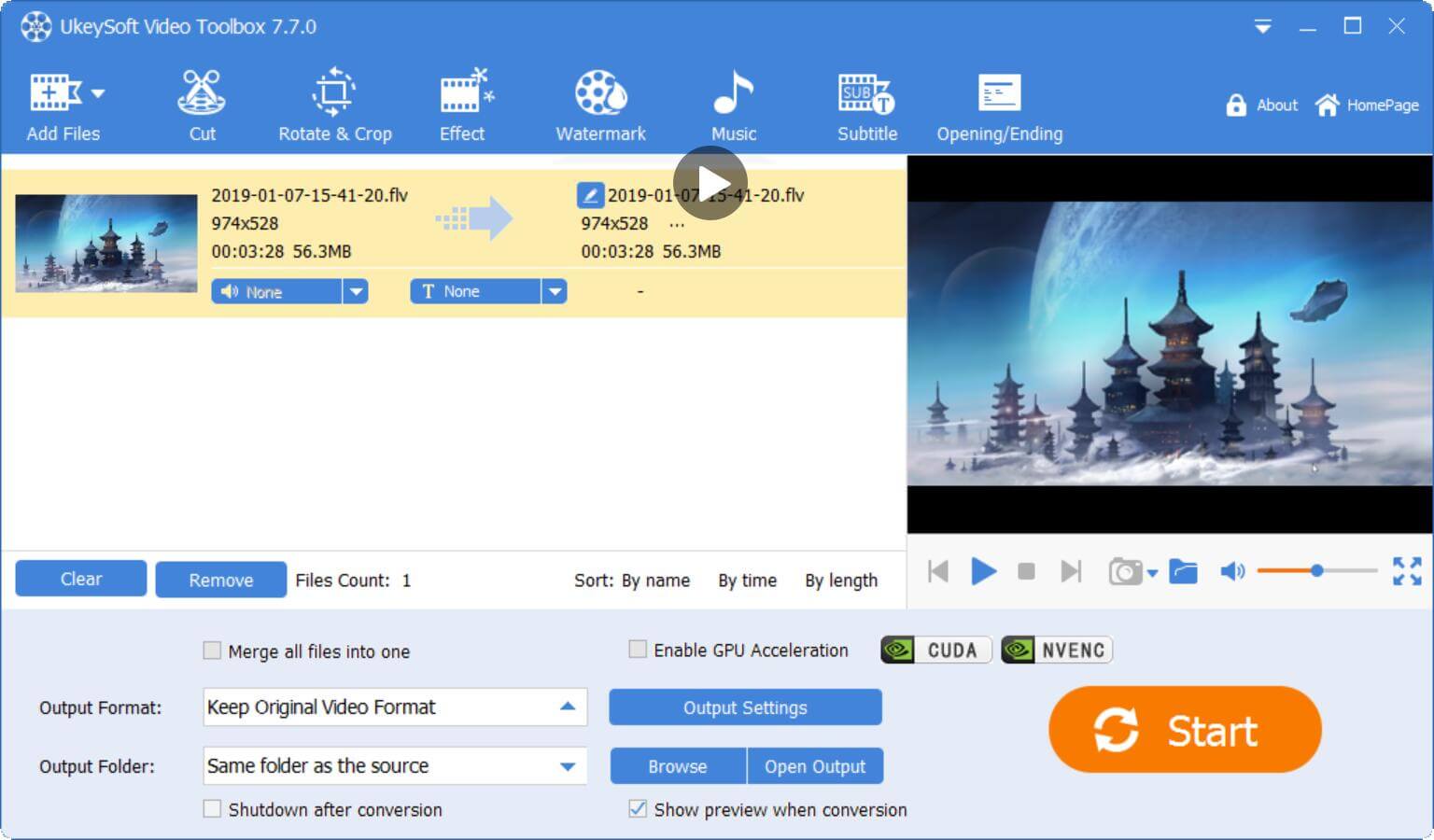
Step 6. Edit Recorded Zoom Meeting
After recording finished, you can also edit and modify the conference video by "Video Toolbox" function, such as cutting off the unwanted parts of the video, or adding subtitles or watermarks, music, etc. to the video.
Now you can save the recorded Zoom video to your local drive and keep the videos for playback at anytime, anywhere.
Conclusion
In this article, we demonstrate the common Zoom vulnerabilities and how to fix Zoom vulnerabilities in 5 security measures. To use Zoom more safely, we recommend a tool to record Zoom meeting to local drive for playback at anytime, anywhere. In this way, you can record Zoom meeting safely.
Prompt: you need to log in before you can comment.
No account yet. Please click here to register.

Enjoy safe & freely digital life.
Utility
Multimedia
Copyright © 2024 UkeySoft Software Inc. All rights reserved.
No comment yet. Say something...